Over 485,000 Ubiquiti devices exposed to DDoS attack
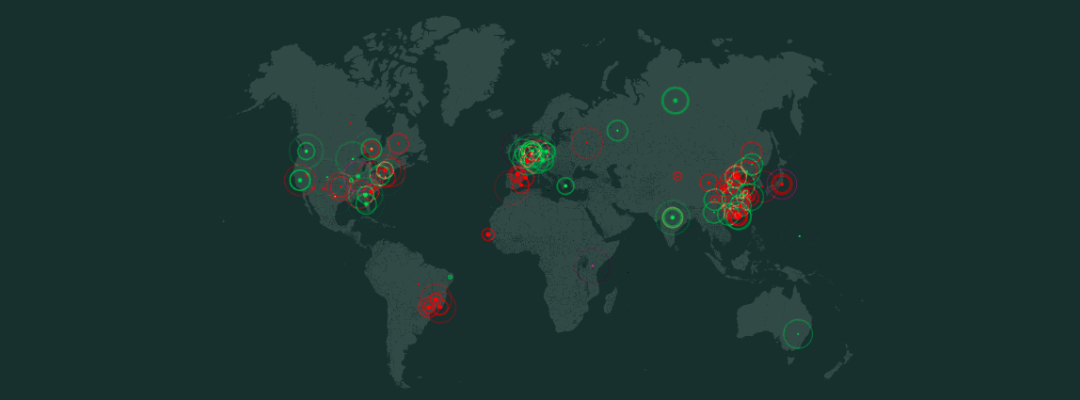
According to an internet scan conducted by US cyber-security firm Rapid7, this vulnerability affects over 485,000 devices around the world. Most of the exposed devices are located in Brazil, followed by the US, Spain and Poland.
The vulnerability is not specific to one Ubiquiti device, and is found on a wide variety of the vendor’s high-grade WISP equipment. The majority of the exposed Ubiquiti devices are NanoStation, AirGrid, LiteBeam, PowerBeam and NanoBeam products, and 17,000 of these devices have already been defaced.
Jon Hart, senior security researcher for Rapid7, states in a security alert that attackers are exploiting a “discovery service” running on port 10,001. Ubiquiti included it on its devices so that the company and internet service providers (ISPs) can use it to find them on the internet and in closed networks. This service has been exploited by attackers to carry out DDoS amplification attacks.
These attacks were first spotted by Jim Troutman, co-founder of NNENIX (Northern New England Neutral Internet Exchange). According to Troutman, attackers are sending small packets of 56 bytes to port 10,001 on Ubiquiti devices, that are reflecting and relaying the packets to a target IP address amplified to a size of 206 bytes.
The exploitation attempts are still in an initial stage but, according to Rapid7, the amplification factor – that is currently 3.67 – can go up to 30-35. Attackers could find a way to carry out DDoS attacks in excess of 1Tbps, which is described by Rapid7 as “a crippling amount of traffic to all but the most fortified infrastructure”.
At the moment this discovery protocol “does not appear to suffer from multi-packet responses”, as we read in Rapid7’s security alert. This makes exploitation extremely hard as attackers can only “reflect” small amounts of DDoS traffic.
Ubiquiti already announced that it was preparing a security patch even if, in its current form, the protocol does not seem to be particularly harmful.
“To our current knowledge, this issue cannot be used to gain control of network devices or to create a DDoS attack,” Ubiquiti Networks said. “As a temporary workaround for this issue while it is being investigated and resolved by the development team, network operators can block port 10,001 at the network perimeter,” the hardware maker added.
Even though the biggest exploitation attempts have only been discovered recently, Rapid7 said that the first attacks attempting to exploit Ubiquiti’s discovery service were detected last July, when several Ubiquiti users reported problems related to the access of SSH services on their Ubiquiti equipment.
Related articles:
https://www.classichotspot.com/blog/update-2019-the-list-of-supported-openwrt-wireless-access-points-vendors/
